(For example, U.S. social security numbers)
QUESTION: I want to encrypt social security numbers (e.g., to avoid potential security problems with sending data work overseas). However, I still want to maintain the ability to match social security numbers to merge files, run gain/loss analysis, check for duplicate keys, and so forth. Can I do this?
ANSWER: Yes. The Social Security Number Encryption tool (outside of ProVal) can be used to encrypt or decrypt the social security numbers (SSNs) in ProVal databases. This tool gives you the ability to restrict specific ProVal users from seeing the real SSN while retaining the ability to match social security numbers, to, for example, merge files, run a gain/loss analysis, check for duplicate keys, and so forth.
Two files, ENCRYPTLIST.TXT and ENCRYPT.BAT, are required in order to encrypt social security numbers. The file ENCRYPTLIST.TXT contains the list of folders containing ProVal clients whose databases have social security numbers that need to be encrypted, whereas the file ENCRYPT.BAT is a batch file that contains the commands required to perform the encryption. (Note: List the location of the ProVal client, i.e., library files, even if the client’s ProVal databases are stored in a different folder.) As expected, another batch file, DECRYPT.BAT (similar to ENCRYPT.BAT), is required to perform the decryption.
To encrypt one or more clients:
-
All three files mentioned above must be in the same folder. Select a suitable folder to store them in – the use of the ProVal working directory (as defined in the ProVal License Server Installation Guide – or see your IT professional), which contains the PROVAL.INI file, is generally recommended.
-
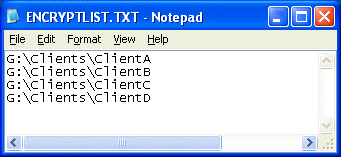
Create the ENCRYPTLIST.TXT file and list the names of client folders in this file, as shown:
-
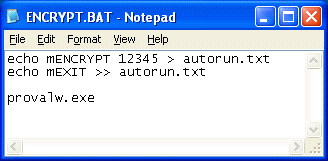
Create the ENCRYPT.BAT file – decide on a numeric encryption key and then type the following commands into the EXCRYPT.BAT file, as shown:
NOTES:
-
The right argument to mENCRYPT shown above, 12345, is the user-supplied encryption key. This key is any non-zero number with at least two digits and will be used in the encryption algorithm. The identical key must be used when decrypting; otherwise the decryption will fail. This allows client managers to encrypt their clients with different keys.
-
The path to provalw.exe must be fully qualified (i.e., identified) in case provalw.exe is not in the folder where the three files are stored (e.g., as in a typical network installation of ProVal).
-
Before the encryption operation starts, ensure that ProVal is not open.
-
Run ENCRYPT.BAT to perform the encryption.
-
The encryption tool logs noteworthy events in a file (that it creates) called ENCRYPTLOG.TXT. It is recommended that this file be reviewed to ensure the success of the encryption operation.
To decrypt one or more clients, a parallel process would be used:
-
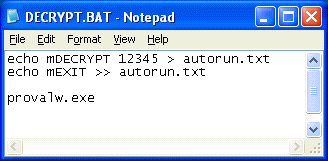
Create the DECRYPT.BAT file: make a copy of the ENCRYPT.BAT file and call it DECRYPT.BAT. (As previously mentioned, store it in the same folder as ENCRYPT.BAT.) Open DECRYPT.BAT and change the mENCRYPT directive to mDECRYPT, as shown:
-
Repeat steps 4-6 above, running DECRYPT.BAT.
NOTES:
-
Importing data into an encrypted database is NOT allowed. The database MUST be decrypted before data is imported.
-
When in ProVal, the user can determine if the database is encrypted by the suffix “<SSNs encrypted>” that appears in the Database window on the bottom of the main ProVal screen.